Cybersecurity Expert Warns of Stealers Exploiting Popular macOS Apps

- #macOS
- #Security
• 9 min read
At Moonlock, the cybersecurity wing of MacPaw, we have been closely monitoring the evolution of various types of macOS malware. Recently, our attention, along with that of cybersecurity researchers worldwide, has been captured by stealers.
Stealers?
A stealer is a type of malware designed to covertly harvest sensitive information from unsuspecting users. In recent years, the prevalence of stealers targeting macOS users has surged dramatically. In 2024 alone, we've observed a 3.4 times increase in unique stealer samples compared to 2023. To put that in perspective, February 2024 alone saw over 1,000 unique samples.
Stealers functionality
To start, let’s examine the commonly used techniques identified in various macOS stealer samples.
Phishing for credentials: Threat actors craft deceptive prompts that could easily pass for legitimate macOS dialogs. These prompts trick users into providing passwords and other credentials under the guise of necessary steps to install or update applications.
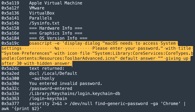
Targeting sensitive information: Stealers search for personal and banking data through system directories and macOS-specific applications, extracting information from Safari, Chrome, and even securely stored details in Keychain.
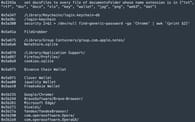
System profiling: Hackers gather extensive details about the user’s hardware and software configuration by leveraging macOS’s built-in tools. This information helps them tailor further attacks.
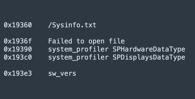
Data exfiltration: To stealthily exfiltrate sensitive data, malware typically establishes a secret folder within users’ home directories and communicates with Command and Control (C2) server.
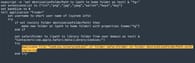
Distribution of stealers
Threat actors typically advertise their stealers on underground forums, seeking partners to distribute them not only through phishing emails but also through SEO manipulation and Google Ads.
This strategy leverages search engine optimization to push malicious websites to the top of search results, luring unsuspecting users into downloading compromised software. It’s a prime example of why you shouldn’t always trust Google Search results. Cybercriminals can exploit SEO mechanisms to promote their malware.
Stealers in Google Ads
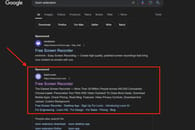
Moonlock exposed one such case, dubbed the Loom impersonation, but it was later confirmed that the stealer targeted a much broader range of apps.
In this instance, a macOS stealer malware posing as the Loom app was probably linked to the Crazy Evil group, as uncovered by Moonlock Lab during our investigation of a sophisticated campaign involving deceptive Google-sponsored URLs and malicious clones of popular applications. Indeed, Moonlock Lab's research later revealed that this campaign extended beyond Loom. The attackers also created fake versions of other popular applications, including Figma, TunnelBlick (VPN), Callzy, and an intriguing case named BlackDesertPersonalContractforYouTubepartners[.]dmg. In other words, threat actors distribute stealers in widespread campaigns targeting a diverse array of popular applications.
The high-profile story was reported by prominent media outlets, including AppleInsider, 9to5mac, MacWorld, and MacMagazine, further amplifying the significance of the threat of stealers.
Read more in the Moonock investigation.
Uncovering stealers: Ledger case
We in Moonlook have been constantly monitoring darknet forums and threat actors’ Telegram channels to discover current and emerging stealers. Speaking of Telegram it has been in the headlines lately following the arrest of its founder, Pavel Durov, who faces accusations of complicity in cybercrimes, among other charges. In our monitoring, we've observed that cybercriminals indeed use Telegram as a platform for selling stealers and recruiting distribution partners.
This proactive approach allows us to catch the latest developments and tactics before they become widespread. A great example is a Telegram channel operated by the creators of the AMOS stealer.
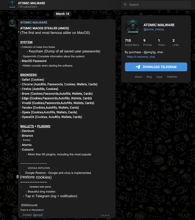
This channel not only facilitates the sale of their malware but also provides real-time updates on development and deployment strategies. By keeping a close eye on the posts in this channel, we were even able to create a timeline of updates of the AMOS stealer.

Furthermore, we spotted an announcement of a feature that stood out. It was the capability to look for the legitimate LedgerLive app on a victim’s device and replace it with a malicious clone.
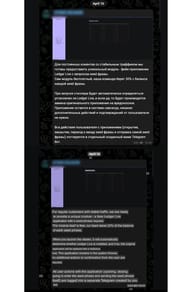
LedgerLive is a widely used application for managing cryptocurrency wallets, providing users with a secure and convenient way to handle their digital assets. Consequently, due to its popularity and the high value of the assets it manages, it has become a lucrative target for cybercriminals.

Infection chain
We hunted down the brand new malware module from a threat actor to analyze how it steals digital assets from unsuspecting users.
As noted, the attack begins with a user downloading a malicious installer disguised as CrackInstall.dmg. Inside this seemingly harmless file is the Mach-O stealer, designed to execute silently once opened.
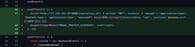
Upon execution, the stealer gets to work, replacing key components in the LedgerLive app.

Specifically, it targets files such as App.tsx, PairMyNano.tsx, and ProtectDiscoverBody.tsx, replacing them with malicious versions.
This process effectively creates a clone of the original LedgerLive app, designed to mimic the legitimate app's appearance and functionality, making it difficult for users to detect the compromise.

As a consequence, the infected LedgerLive app starts to show a window that prompts users to enter their seed phrases – a set of words used to recover cryptocurrency wallets. The message is as follows: “Your secret phrase is the secret list of words that you backed up when you first set up your wallet. Ledger does not keep a copy of your recovery phrase.”
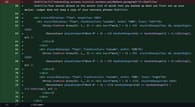
Data Transmission to Command and Control Servers
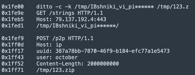
After capturing the seed phrases, the malware sends the information to a C2 server at http://159[.]65[.]193[.]64:8080/statistics. This primary server receives the sensitive information, which can then be exploited by the hackers, leading to financial losses for users.
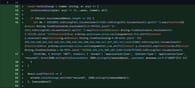
Additionally, the malware transmits user data and execution status to a secondary server at http://77[.]221[.]151[.]29:8080/. For attackers, this multi-layered approach to data exfiltration ensures they receive comprehensive information about the infected systems.

Social Engineering
While the case of replacing the LedgerLive app is fascinating, it’s just the tip of the iceberg. Many users are now vulnerable to stealers, as evidenced by the increasing number of detections among them.
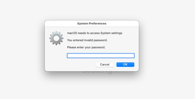
How exactly are these stealthy malware applications able to infiltrate so many devices? The answer largely lies in social engineering. All these stealer samples have one thing in common: they bypass macOS's built-in security features, specifically Gatekeeper. In our lab, we often observe a typical Gatekeeper bypass technique where the malware displays a fabricated security prompt. This prompt guides the user to open their system preferences and allow a blocked application. These visuals look like legitimate macOS prompts, making them highly effective at deceiving users.

Conclusion
The rise of macOS malware like the AMOS stealer underscores the importance of vigilance and caution. The case of the malicious LedgerLive clone illustrates how easily trusted applications can be compromised, leading to significant financial losses for users. Each of us can be targeted by cybercriminals, and there is a growing interest in such activities. There are forums not just for individuals but for entire teams where threat actors advertise stealer software to those who can distribute it, even using trusted platforms like Google Sponsored links.
To protect yourself, always download software from official sources, avoid clicking on suspicious links, and use robust security tools like CleanMyMac X with Moonlock Engine to detect and block such threats.
Indicators of Compromise
Diff of infected and original LedgerLive app: GitHub Gist
| 304145c8c242644a7aa866383bdac3c169f944ea8c6656b663c223da1359fbb9 | CrackInstall.dmg |
| 0822cf5c34341d124164b1c89889dedc405034e40fd0c8a219859a2561a289ee | Mach-O |
| 5c9e197c4e7752e6a15fc9077fa41dc78ac5a737ae73a01ddb6b6fc6aadd1f1c | Malicious LedgerLive App Component App.tsx |
| 8c23db010886261cb27a5fbaa45502586f4031cc60bda3a8df778d94a3335888 | Malicious LedgerLive App Component PairMyNano.tsx |
| 9d5bcbdc139561951256a43cc05dda3e18da99ffd200975bbf0732e90a97c710 | Malicious LedgerLive App Component ProtectDiscoverBody.tsx |
| 1e86fd2688e7d0086e243194504318c125a5a7c8a1ef6f42bf39bd90deba793b | Malicious LedgerLive App Component app.asar |
This is an independent publication and it has not been authorized, sponsored, or otherwise approved by Ledger SAS.