How to Use GitHub Dependabot

- #Web
• 7 min read
What to do with weird Dependabot alerts? Set it up to automate dependencies upgrades and so much more.
When it comes to Dependabot, most developers think of strange pull requests and alerts in GitHub.


In reality, Dependabot is a powerful tool that every developer should use to ship better code. Its main purpose is to help you keep the supply chain secure. Let's look at what GitHub Dependabot is and how to make the most of it.
Security of your code starts with the simplest things: ensuring your packages are up-to-date and don’t contain any malware. The trivial task can be painful. Sometimes, the dependencies are so far out of date that it’s a nightmare to maintain.
To help developers with this basic but vital task, GitHub offers Dependabot alerts. You’ll get an alert when Dependabot detects insecure dependencies, such as outdated packages or malware. Dependabot will automatically open pull requests to update vulnerable packages.
How to enable Dependabot Alerts

By default, all new GitHub repositories come with active Dependabot alerts.
“Dependabot alerts – Active” means that alerts are enabled for this repo. You don’t need to worry about your dependencies being a threat. If the vulnerability has been fixed with a patch release, Dependabot will automatically open a pull request to the default branch. You can view a detailed analysis of the identified vulnerabilities in security advisories.
In addition to upgrading vulnerable dependencies, GitHub Dependabot also supports so-called version updates. The bot automatically updates repository dependencies: packages (different ecosystems and even multiple ecosystems for the same repository) and applications (like GitHub Actions).
You can also enable Dependabot manually.
Option 1: Enable manually
To enable this option, simply add the dependabot.yml configuration file to the .github folder at the root of the repository.
repoRoot/.github/dependabot.yml
Option 2: Enable using UI
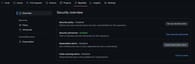
If Dependabot alerts are turned off, go to the “Security” tab in your repository and click Enable Dependabot alerts.
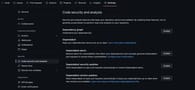
Another option is to do this in “Settings” under “Code security and analysis”. Click Enable to turn on Dependabot alerts.
Here, you can also enable two additional features. “Dependabot security updates” will open pull requests to resolve alerts automatically. “Dependabot version updates” will keep dependencies up-to-date.
See GitHub Docs to learn more about Dependabot security updates and alert settings.
How to configure Dependabot
Configure Dependabot to your needs by overriding the default behavior.
Step 1: Create a config file
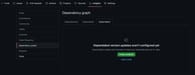
Inside the repository, go to the “Insights” tab and navigate to “Dependency graph”. Under “Dependabot”, click Create config file to create the dependabot.yml file.
Step 2: Configure dependabot.yml
The configuration file contains these keys:
directory. The manifest location lists all existing dependencies for the current ecosystem or multiple manifests for the same or different ecosystem.schedule.interval. The update interval sets the frequency of updates to daily, weekly, monthly, etc.open-pull-requests-limit. You may need the limit during the first launch when Dependabot tries to update many dependencies.reviewers. Assigns reviewers to automatic pull requests.target-branch. Sets the branch related to newly created pull requests and other configurations.
GitHub Docs will help you set up your configuration file.
Put Dependabot to work
After you commit and merge dependabot.yml, the bot will start working. Now, it monitors your packages in real time and performs automatic updates. You can see the version update status in “Insights” under “Dependency graph” or even check manually for updates.
What happens next? When Dependabot detects an outdated dependency, it creates a pull request to update the package to the latest version in the manifest. Review the change log and release notes to check if the tests were successful. Next, Dependabot will add all the links to the pull request description. Approve, merge, done!
To summarize, Dependabot can open pull requests in two cases:
- Dependabot security updates – automatic pull requests updating dependencies with known vulnerabilities.
- Dependabot version updates – automatic pull requests updating dependencies to the last possible version regardless of vulnerabilities.
Dependabot is super awesome. It’s available out of the box from GitHub for free. You can automate it with Actions and use countless built-in functions.
Another cool thing about Dependabot is the support of different ecosystems. You can have a monorepo with PHP on the backend and composer.json and JS on the frontend with package.json. Dependabot will update all the different ecosystems according to the specified rules. It works fine with npm workspaces.
Tips and pointers
In general, GitHub Dependabot offers excellent functionality, but there are some pains our developers have revealed over time.
Too many pull requests
There can be a lot of pull requests. If each request is related to a working branch (develop or main__), Dependabot triggers an avalanche of CI builds.
Recommended solution: Configure the creation of pull requests in a separate branch.
Branch protection rules must be updated regularly from the default. Setting them up may be problematic. You’ll have to think of a way to automatically open pull requests from that branch to the default. We solved this challenge by using GitHub Actions.
Conflict in other pull requests
Sometimes, merged pull requests cause conflict with other opened pull requests. In this case, Dependabot will rebase and trigger pull request rebuilds again. It's impossible to group requests with multiple updates in Dependabot. As a result, you’ll have to spend too much time grouping minor/patch versions and opening major versions in separate pull requests.
Recommended solution: Integrate third-party tools for more functionality.
Dependabot is enough for most developers out there. However, if you need something more powerful, take a look at these tools.
Take your dependencies game to a whole new level
The following tools complete the same tasks as Dependabot but also provide additional functionality, broader ecosystem support, and convenient UI. However, they don’t come out of the box and usually have paid plans.
Snyk
Snyk is a general security tool with robust functionality. It matches everything Dependabot offers and provides a user-friendly interface for controlling version updates. Snyk is the best option for developers who already use Snyk Security Tools.
Snyk’s basic version is free. There are several customizable paid plans with more advanced features and unlimited use.
Depfu
Depfu doesn’t require additional configuration files in the repository. It offers a UI-based setup and neat dashboard. Depfu works with GitHub through API. Unlike Dependabot, Depfu doesn't open requests immediately to the update. Further, the tool analyzes version release frequency and allows regular PRs for all pending updates.
Depfu offers a free plan for limited personal use and several paid options for teams and businesses.
Renovate
Renovate is an easily-configured open-source tool for updating dependencies. It can be self-hosted or used like a GitHub App. Renovate has three key features:
- Automatic detection of manifest files.
- Community-offered replacements for deprecated dependencies (npm packages only).
- Separate pull requests for all patch, minor, and major updates.
Renovate is an open-source project, so it's completely free of charge.
Try Dependabot yourself
Don't freak out the next time you get a weird Dependabot alert. It’s there to help you. After all, meticulously checking whether all your packages are up-to-date takes precious time and effort. Thankfully, GitHub automatically scans for insecure packages with Dependabot and alerts you if it finds potential security vulnerabilities.
Dependabot use might get tiresome in really complex projects. If, one day, you find yourself spending too much time grouping conflicting PRs, consider powerful third-party tools such as Snyk, Depfu, or Renovate.
The bottom line is mastering Dependabot and configuring alerts to suit your preferences will save time and help maintain a secure supply chain.
Resources
Dependabot Documentation
This is an independent publication and it has not been authorized, sponsored, or otherwise approved by GitHub Inc.